What is Ransomware?
Ransomware is a type of malware, or malicious software. You can read our What is Malware article if you’re not sure what ransomware is. It is specifically designed to completely block access to a computer system until a sum of money (often in Bitcoin) is paid to the hacker(s).
How does Ransomware Work?
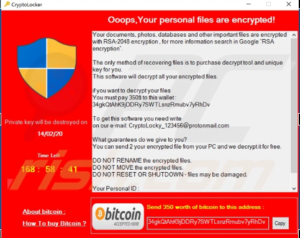
We discussed how malicious files find their way onto a businesses network in the article linked above. Once on network, there are multiple ways that ransomware will begin to infect a businesses network. Regardless of the approach, the end goal is to lock every user out of the network. Hackers will spend months monitoring network activity in an effort to understand each and every system before enacting the ransomware. Once enacted, one or all end users will receive a message that goes something like this:
What Happens Next?
From here, you have only two options. First, pay the ransomware and hope that the hackers provide you with the access key to unlock your data. Second, find an IT company with the ability to recover your data. Both can be expensive products, and the decision that gets made always depends on the state of a company’s backups, and the portections put in place prior to the encryption.
Read more about removing malware from your network.
The Layered Approach
The best way to prevent any type of malware, including ransomware, is to take a layered approach to IT security. This means that we deploy multiple security controls throughout a network, each making it increasingly difficult for a cyberattack to occur.
Human Layer – Humans are the first, and weakest part of your security controls. As a result, this is often where most ransomware attacks begin. Training employees on how to identify phishing attempts, and implementing Dark Web Monitoring can help prevent problems in this security layer.
Physical Layer – These are the things that automatically identify suspicious activity through the implementation of next-gen firewall services such as Intrusion Detection and Prevention, SIEM Logging, and other services.
Network Layer – These are the configuration and services (including web filtering) designed to work with your connectivity services, including VPNs.
Endpoint Layer – This is done by making use of next-gen antimalware, and breach detection services, patch management, endpoint detection programs, and remote monitoring services. These next-gen services are designed to be smarter than traditional services, and can often weed out malware at an exponentially higher rate than traditional signature-based programs.
Application Layer – Includes vulnerability scanning, which is deployed to search for vulnerable versions of software being used.
Policy Layer – These are the rules and procedures that employees follow. This may have to do with how they are allowed to use company data and devices, whether or not they can use their own devices (BYOD), as well as the rules for peripheral endpoints (e.g., wireless access points configurations for guest access to your network).
Data and Backup Layer – This refers to how data is transferred and stored, as well as how data is backed up. You can read more about backups in our 3-2-1-1 rule article.
Conclusion
There are many hardware and software solutions to help provide protection for your company. Equally important as selecting the correct devices and programs is steps taken to properly design your infrastructure, and the layers of protection.
No ransomware prevention strategy is complete without a recurring review of the hardware, software, and policies set. As technology advances, so does the strategy that hackers take. It’s important to update your strategy on an annual basis.
To reach CTS Companies, find our Contact Us Page, or simply search for IT Services in Michigan. Also, we have an updated article on Cybersecurity Trends in 2023. Finally, learn more about the how cybersecurity concerns have impacted disaster recovery.
