Cybersecurity Companies in Rochester, MI
Cybersecurity Companies in Rochester, MI Simplified
Safeguarding your company and assets does not have to be difficult, and you don’t have to be an expert in order to protect what you do.
That’s why we exist, to help you make well informed decisions, so you can focus on what’s important to you.
This means that we select a solution from our best-of-breed security stack that works within your budget and needs – not the other way around..
The CTS Managed CyberSecurity Service Process
CTS’ Business Technology Experts will assess your network before making any recommendations. We will never make a recommendation that is not well-suited to your business needs. We will always provide you with enough information to make well-informed decisions. Your dedicated Network Engineer will work on your timeline to get the job done. Finally, our Security Operations Center will continue to monitor your network, every second of every day.
Managed Security
Our Managed Security Service bundles multiple security tools, and integrates with our ticketing and Security Operations Center (SOC). You don’t have to be a large corporation to leverage advanced tools.
Compliance Services
CTS’ Compliance Service will save you (literally) up to hundreds of hours per year in managing one or more compliance frameworks. For HIPAA, PCI, SOC, NIST, ISO. CMMC, FedRAMP (many more), we will deliver:
- Automation to reduce manual and repetitive workloads
- Automated + Ongoing Adherence Monitoring
- Automated Policy generation
- Task Management for accountability and follow-up
- Auditable Reporting
- Scanning using built-in tools
- Import tool for external scans (penetration tests, Vulnerability Scans, Nessus, Qualys, and Microsoft Secure)
- Periodic Reviews of Status and Progress
Penetration Testing
Ransomware
Managed Detection and Response (MDR)
Today, it’s imperative to have the right people in place as well. CTS’ Security Operations Center (SOC) will monitor logs from our Detection and Response technology to verify what is (and is not) a real threat. We’ll reduce ticket fatigue, and increase your confidence in your security technology stack.
Encryption and DLP
Backup/Recovery
RMM
Employee Security Training
- Our Security Training tools will equip your employees with the knowledge and confidence to protect themselves, as well as your organization. It is a fact: not all security threats are carried out using malicious software. In fact, the majority of issues start with ‘social engineering’ – a tactic to trick an employee into doing something they should not. Equip your employees with the ability to identify bad actors, and what to do when your business becomes a target.
- SIEM Logging – Our managed services with SIEM capabilities will aggregate SIEM logs from disparate sources (firewall, EDR, Microsoft 365, etc), and funnel them to our Security Operations Team (SOC). Our SOC team will analyze every flagged item, assess the threat and urgency, provide remediation steps, and integrate the information into CTS’ ticketing system, to which you have access.
An Overview of Cybersecurity Companies in Rochester, MI
Technology should exist only to help you do what you do best – to run your business. While the security technologies deployed over the last 45 years have changed, our commitment to delivering the best-of-breed technology stack has not.
Continue to do what you do best, and let CTS handle the rest.
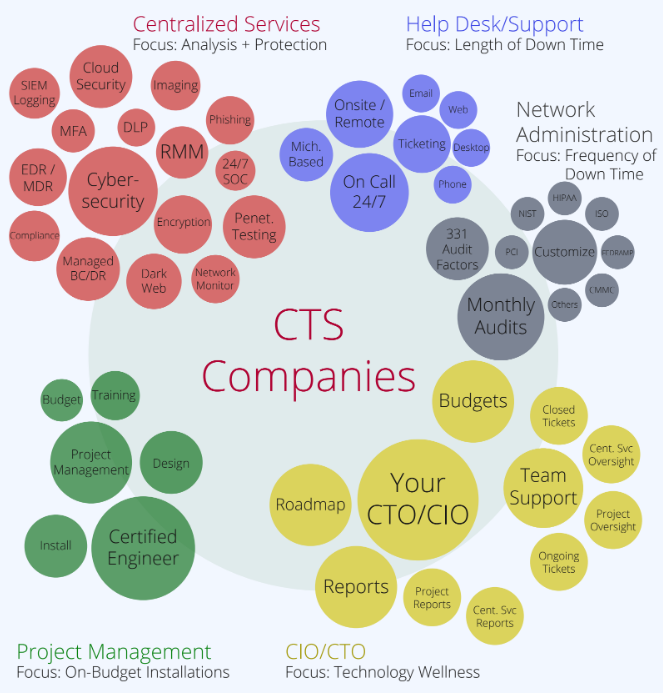
An Overview of Cybersecurity Companies in Rochester, MI
Technology should exist only to help you do what you do best – to run your business. While the security technologies deployed over the last 45 years have changed, our commitment to delivering the best-of-breed technology stack has not.
Continue to do what you do best, and let CTS handle the rest.

What Our Clients Are Saying
Why CTS Companies?
Your Managed Security Services Provider must know that technology does not exist within a vacuum – there is more to consider than simply leveraging the best technology. Matching the right solution to your business is the best way that we can add value. We also provide 24/7 support, which is included in most of our service plans.

Why CTS Companies?
